Configuring Teleworker VPN Client Group Policies
- Vpn Client Tai Mien Phi
- Cisco Teleworker Vpn Client
- Vpn Gate Client
- Cisco Rv340 Teleworker Vpn Client
- Vpn Gate
- Softether Vpn Client
- Teleworker Vpn Client
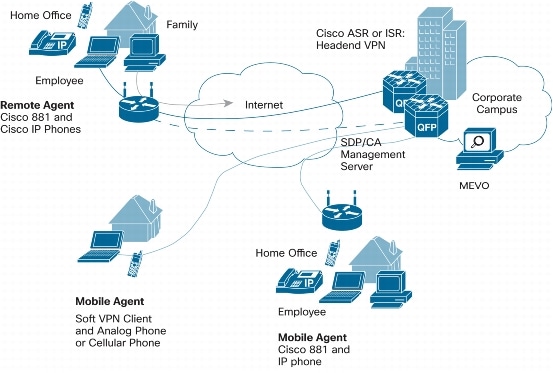
Teleworker VPN and Layer 3 roaming with a concentrator both use the same Meraki Auto VPN technology. Wireless access points should concentrate to a Meraki MX security appliance. It is recommended that a separate network be created in dashboard for each remote site location for purposes of manageability and usage tracking. For RV325, need suggestions for teleworker VPN client software. As a volunteer church techie I've just installed RV325 in a scenario matching the description of small business. I've achieved port-forwarding from the outside world to a dummy host that is not mission-critical. So far, so good. Configuring Teleworker VPN Client. The Teleworker VPN Client feature minimizes the configuration requirements at remote locations by allowing the security appliance to work as a Cisco VPN hardware client to receive the security policies upon the VPN tunnel from a remote IPsec VPN server. Learn how to configure MAC VPN Client in VPN settings on RV340 Series Routers. For additional support information, visit the Cisco Small Business Support Com.
To be able to complete the configuration of a Teleworker VPN Client group policy, you must have the following information ready.
•IPsec VPN server’s IP address or hostname.
•IPsec VPN server’s group policy name.
•Pre-shared key or digital certificates for IKE authentication.
Note Up to 16 Teleworker VPN Client group policies can be configured on the security appliance. You can create multiple group polices to connect to different VPN servers but only one VPN connection can be active at a time.
1.Click VPN > Teleworker VPN Client.
2.To add a group policy, click Add.
Other Options: To edit an entry, click the Edit (pencil) icon. To delete an entry, click the Delete (x) icon. To delete multiple entries, check them and click Delete.
The Teleworker VPN Client - Add/Edit window opens.
3.In the Basic Settings tab, enter the following information:
•Description: Enter the name for the group policy.
•Server (Remote Address): Enter the IP address or domain name of the remote IPsec VPN server.
•Activate Connection on Startup: Click On to automatically initiate the VPN connection when the security appliance starts up, or click Off to disable it. Only one VPN connection can be active on startup.
•IKE Authentication Method: The VPN client must be properly authenticated before it can access the remote network. Choose one of the following authentication methods:
–Pre-shared Key: Choose this option if the IPsec VPN server uses a simple, password-based key to authenticate and then enter the following information:
Group Name: Enter the name of the IPsec Remote Access group policy that is defined on the IPsec VPN server. The security appliance will use this group policy to establish the VPN connection with the IPsec VPN server. The IPsec VPN server pushes the security settings over the VPN tunnel to the security appliance.
Password: Enter the pre-shared key specified in the selected group policy to establish a VPN connection. The pre-shared key must be entered exactly the same here and on the IPsec VPN server.
–Certificate: Choose this option if the IPsec VPN server uses the digital certificate from a third party Certificate Authority (CA) to authenticate. Select a CA certificate as your local certificate from the Local Certificate drop-down list and select the CA certificate used on the remote IPsec VPN server as the remote certificate from the Peer Certificate drop-down list for authentication.
NOTE: You must have valid CA certificates imported on your security appliance before choosing this option. Go to the Device Management > Certificate Management page to import the CA certificates. See Managing Certificates for Authentication, page 350.
•Mode: The operation mode determines whether the inside hosts relative to the Cisco VPN hardware client are accessible from the corporate network over the VPN tunnel. Specifying an operation mode is mandatory before making a VPN connection because the Cisco VPN hardware client does not have a default mode. For more information about the operation mode, see Modes of Operation.
–Choose Client if you want the PCs and other devices on the security appliance’s inside networks to form a private network with private IP addresses. Network Address Translation (NAT) and Port Address Translation (PAT) will be used. Devices outside the LAN will not be able to ping devices on the LAN, or reach them directly.
–Choose NEM (Network Extension Mode) if you want the devices connected to the inside interfaces to have IP addresses that are routable and reachable by the destination network. The devices at both ends of the connection will form one logical network. PAT will be automatically disabled, allowing the PCs and hosts at both ends of the connection to have direct access to one another.
•VLAN: If you choose NEM, specify the VLAN that permits access from and to the private network of the IPsec VPN server.
•User Name: Enter the username used by the Teleworker VPN client to establish a VPN connection.
•User Password: Enter the password used by the Teleworker VPN client to establish a VPN connection.
4.In the Zone Access Control tab, you can control access from the zones in your network to the remote network if the Teleworker VPN client works in Client mode. Click Permit to permit access, or click Deny to deny access.
NOTE: The VPN firewall rules that are automatically generated by the zone access control settings will be added to the list of firewall rules with the priority higher than the default firewall rules, but lower than the custom firewall rules.
5.In the Advanced Settings tab, enter the following information.
•Backup Server 1/2/3: Enter the IP address or hostname for the backup server. You can specify up to three servers as backup. When the connection to the primary IPsec VPN server fails, the security appliance can initiate the VPN connection to the backup servers. The backup server 1 has the highest priority and the backup server 3 has the lowest priority.
NOTE: The Teleworker VPN client can get the backup servers from the IPsec VPN server during the tunnel negotiation. The backup servers specified on the IPsec VPN server have higher priority than the back servers specified on the Teleworker VPN client. When the primary connection fails, first try to connect to the backup servers specified on the IPsec VPN server, and then try to connect to the backup servers specified on the Teleworker VPN client.
•Peer Timeout: Enter the value of detection timeout in seconds. If no response and no traffic from the primary server or the backup server over the timeout, declare the peer dead. The default value is 120 seconds.
6.Click OK to save your settings.
7.A warning message appears saying “Do you want to make this connection active when the settings are saved? (Only one connection can be active at a time.)”
•If you want to immediately activate the connection after the settings are saved, click the Activate Connection button. When you create multiple Teleworker VPN Client group policies at a time, only one connection can be active after you save your settings. The security appliance will use the group policy that was last created or edited to initiate the VPN connection.
•If you only want to create the Teleworker VPN client group policy and do not want to immediately activate the connection after the settings are saved, click the Do Not Activate button. You can click the Connect icon to manually establish the VPN connection.
NOTE: This feature is different from the Active Connection on Startup feature. It is used to activate the connection immediately after the settings are saved, but the Activate Connection on Startup feature is used to activate the connection when the security appliance starts up.
8.Click Save to apply your settings.
Objective
Vpn Client Tai Mien Phi
The Teleworker VPN Client feature minimizes the configuration requirements at remote locations by allowing the device to work as a Cisco VPN hardware client. When the Teleworker VPN Client starts the VPN connection, the IPSec VPN server pushed the IPSec policies to the Teleworker VPN Client and creates the corresponding tunnel.
This article aims to show you how to configure the Teleworker VPN Client on the RV34x Series Router.
Applicable Devices
- RV34x Series Router
Software Version
- 1.0.01.17
Configure the Teleworker VPN Client
Step 1. Log in to the web-based utility and chooseVPN > Teleworker VPN Client.
Step 2. In the Teleworker VPN Client area, click the On radio button to enable the Telework VPN Client.
Note: Only a single Teleworker VPN Client can have an active connection at startup.
Step 3. (Optional) In the Auto Initiation Retry area, click a radio button On or Off to enable or disable an automatic initiation attempt after a failure. Clicking On means that the router will attempt to make an initiation after failure.
Note: In this example, On is chosen.
Step 4. In the Retry Interval field, enter a value in seconds that the router will make an attempt to make an initiation to connect. The default is 120 seconds.
Note: In this example, the default value is used.
Step 5. In the Retry Limit field, specify the number of times the router will automatically attempt to make an initiation after a failure.
Note: In this example, the number entered is 2.
Configure the Basic Settings
Step 6. In the Teleworker VPN Clients table, click Add to create and configure a Teleworker VPN client.
Step 7. In the Basic Settings area, enter a name for the VPN tunnel in the Name field.
Note: In this example, Dracarys is used.
Step. 8. In the Server (Remote Address) field, enter the IP address of the remote server.
Note: In this example, 128.13.22.12 is used.
Step 9. To initiate a connection upon startup, click Onin the Active Connection on Startup area. To manually start a connection, click Off.
Note: In this example, On is chosen.
Step 10. In the IKE Authentication Method area, choose an authentication method to be used in IKE negotiations in IKE-based tunnel. The options are:
- Pre-shared Key — IKE peers authenticate each other by computing and sending a keyed hash of data that includes the Pre-shared Key. If the receiving peer is able to create the same hash independently using its Pre-shared key, it knows that both peers must share the same secret, thus authenticating the other peer. Pre-shared keys do not scale well because each IPSec peer must be configured with the Pre-shared key of every other peer with which it establishes a session. If this is chosen, proceed to the next step.
- Certificate — The digital certificate is a package that contains information such as a certificate identity of the bearer: name or IP address, the serial number expiration date of the certificate, and a copy of the public key of the certificate bearer. The standard digital certificate format is defined in the X.509 specification. X.509 version 3 defines the data structure for certificates. If this is chosen, skip to Step 13.
Note: In this example, Pre-shared Key is chosen.
Step 11. If you have chosen Pre-shared Key in Step 10, enter a group name in the Group Name field.
Note: In this example, FreeFolk is used as the Group Name.
Step 12. In the Password field, enter a password to be associated with the Group.
Step 13. If you have chosen Certificate in Step 10, choose the appropriate certificate for your router.
Note: In this example, Default is chosen.
Step 14. Click on a radio button to choose a Mode. The options are:
- Client — This option allows the client to request for an IP address and the server supplies the IP addresses from the configured address range. If this is chosen, proceed to Step 16.
- Network Extension Mode (NEM) — This option allows clients to propose their subnet for which VPN services need to be applied on traffic between LAN behind server and subnet proposed by client. You will also be asked to choose a VLAN. If this is chosen, skip to Step 15.
Note: In this example, Client is chosen.
Step 15. If NEM was chosen in Step 14, choose a VLAN from the drop-down list. The options may vary depending on pre-configured VLAN settings.
Note: In this example, 25 is chosen.
Cisco Teleworker Vpn Client
Step 16. In the User Name field, enter a user name to be associated with the Telework VPN Client.
Note: In this example, Tormound is used.
Step 17. In the User Password field, enter a password for the username.
Step 18. In the Confirm User Password field, re-enter the password to confirm the password. If the incorrect password is entered, the field will turn red.
Step 19. Click Apply to save the settings.
Step 20. A pop-up window will appear asking you to activate the connection as the settings are saved. Click the Activate Connection button to confirm the activation and Do Not Activate button to activate the connection later.
Note: In this example, Activate Connection is chosen.
Vpn Gate Client
You will be taken back to the main Teleworker VPN Client page.
You should now have successfully configured the basic settings for the Teleworker VPN Client on the RV34x Series Router.
Configure the Advanced Settings
Step 1. (Optional) In the Backup Server 1 field, enter the IP address or the domain name of the backup server. This will be where the device can start the VPN connection in case the primary IPSec VPN server fails. You can enter up to three backup servers in the fields provided. The Backup Server 1 has the highest priority among the three servers and the Backup Server 3 has the lowest.
Note: In this example, brienneoftarth.com is used.
Step 2. In the Peer Timeout field, enter the time in seconds a peer can remain idle before disconnecting. The range is from 30-480 seconds. The default is 120.
Cisco Rv340 Teleworker Vpn Client
Step 3. Click Apply.
You should now have successfully configured the Advanced Settings of the Teleworker VPN on the RV34x Series Router.
Vpn Gate
Click on the following links for articles on the following topics:
Softether Vpn Client
View a video related to this article...
Teleworker Vpn Client
Click here to view other Tech Talks from Cisco