Hello ethical hackers and bug bounty hunters. Today, you will learn the top 10 Burp Suite extensions I found myself using over and over again. They assist me in different areas, such as pretty-printing data, actively testing for specific vulnerability classes, parsing API definitions and brute-forcing.
The Burp Suite is an assortment of devices used to perform pen-testing and security inspecting. This tutorial mainly focuses on the free version. The Burp Suite can act as an interrupting proxy and also captures traffic between an internet browser and a web server. The Burp Suite is an assortment of devices used to perform pen-testing and security inspecting. This tutorial mainly focuses on the free version. The Burp Suite can act as an interrupting proxy and also captures traffic between an internet browser and a web server.
Wsdler is your burp extension for SOAP
During your penetration testing or bug bounty hunting, you might encounter SOAP-based APIs. They are web services that you can consume according to a file which describes the actions they expose and how to call them. Limewire for macbook free download. This file is based on the Web Services Description Language (WSDL).
Whenever you find one, you can parse it using Wsdler. Additionally, this Burp extension constructs the HTTP requests as the API expects them.
JSON Beautifier
Before Burp Suite rolled its Pretty button feature, this was the first extension I needed to install after any fresh Burp Suite setup. Nowadays, the majority of web application use RESTful APIs which generally use JSON objects to transfer data between the client and the server. JSON Beautifier prettifies the inline JSON data to make your life easier.
This Burp extension is free and can be used in either Burp Suite Community Edition or Professional.
J2EEScan is a great burp extension for Java EE applications
In my penetration testing assignments, I usually test J2EE web applications, which are Java web applications that support enterprise-level requirements, such as scalability and availability. Therefore, I use J2EEScan to assist me in finding vulnerabilities for the most common CVEs that target J2EE technologies.
The extension adds test cases to the BurpSuite Scanner. Therefore, there no additional configuration after you install it. All you have to do is run a scan and wait for vulnerabilities in the Issue Activity panel in the Burp’s Dashboard tab.
JSON WEB Tokens, the Burp extension, not the standard
According to jwt.io, JSON Web Token is:
[…] an open standard […] that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed.
When you do bug bounty hunting or web application penetration testing, it is a pain to manually copy the tokens from Burp Suite and paste them into your favourite parsing tool, such as jwt.io. This extension allows you to parse the token within Burp, the same way JSON Beautifier prettifies inline JSON objects.
SAML Raider
For those of you who don’t know what SAML, it’s a standard used in Single Sign-On (SSO) for authentication. Here is a brief definition from Wikipedia:
Security Assertion Markup Language (SAML) […] is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based markup language for security assertions.
Since SAML requests contain long base64 encoded XML data, it is impractical to manually parse them. SAML Raider automatically performs the parsing within Burp Suite. Additionally, you can use it to perform known attacks against your target web application. In fact, it comes with pre-configured exploitation techniques, such as signature wrapping, that you can easily run to test for weaknesses in SAML implementations.
AuthMatrix burp extension for broken access control
I’ve already covered this great extension in a Youtube video. It allows you to test for broken access control vulnerabilities, such as IDOR, unprotected endpoints, etc. The flow is fairly simple. Firstly, you browse your target application and send any interesting requests to this extension. Then, you create the target users, such as the attacker and the victim. Then, for each user, you configure the session cookies, and any HTTP headers containing tokens such as JWT or API keys. Lastly, you hit the run button and let AuthMatrix highlight the suspicious requests in red.
HTTP request smuggler
This is the go-to Burp extension when you want to easily detect and exploit a web application through HTTP Request Smuggling.
It detects whether you have a CL.TE or TE.CL condition and reports it directly into Burp Suite’s Dashboard tab, under the Issue Activity menu where all the issues get listed.
If you have no clue about what do CL.TE and TE.CL means, I invite you to read this article from the authors of Burp Suite.
Turbo Intruder
This extension allows you to send large numbers of HTTP requests to a target web application. If you have Burp Community, you know that you can only work with a limited version of the Intruder which does not support multiple threads. Instead, you can use Turbo Intruder.
Since this Burp extension uses a Python snippet that you can edit, I recommend you get familiar with the basics of the Python programming language. That way, you can customize Turbo Intruder to bring more flexibility when you brute force.
Upload Scanner
Whenever you encounter a file upload feature that uses the multipart mime type, I encourage you to give this Burp extension a try. In fact, you can use it to probe the upload features for many security issues.
It fuzzes all the parameters using a set of organized categories that you can choose from. If the application retrieves the uploads, you can configure Upload Scanner to fetch the files to verify cases like XSS.
There are plenty of other features in this awesome Burp extension. I encourage you to learn more about it. Additionally, I prepared this Youtube video to show you how it works.
Java Deserialization Scanner
This Burp extension checks for insecure deserialization issues in Java applications. It uses pre-built serialized java objects to probe the application for a callback. You can configure this feedback to be either a time delay or a callback. If the application sleeps for some time before responding, or if you receive a hit as a callback, the extension highlights exactly what payload has triggered it. Therefore, you can prepare your own payload using tools such as ysoserial.
If you want to learn how insecure deserialization works and how to exploit it with real examples, I invite you to read this article.
Conclusion
There are so many tools, extensions and methodologies available a few clicks away. However, I should mention that you don’t have to use them all. Take some time to discover how they work, then pick the ones that suit your taste and your needs.
Hopefully, this episode has shown you some new Burp extensions that might help you in your next assignment.
Until the next episode, stay curious, keep learning and go find some bugs!
Burp Suite is an intercepting HTTP Proxy, and it is the defacto tool for performing web application security testing. Burp is highly functional and provides an intuitive and user-friendly interface. Its proxy function allows configuration of very fine-grained interception rules, and clear analysis of HTTP messages structure and contents. The proxy can also be configured to perform automated matching and replacement of message headers, and provides an in-browser interface for viewing the proxy cache and reissuing individual requests.
Of all the integrated tool suites, Burp is the only one that implements a fully functional web application spider, which parses forms and JavaScript, and allows automated and user-guided submission of form parameters.
Below we’ve listed out the top 19 plugins which are open source and can be integrated under Burp as an extenders which are as follows:
1. AuthMatrix
AuthMatrix is an extension to Burp Suite that provides a simple way to test authorization in web applications and web services. With AuthMatrix, testers focus on thoroughly defining tables of users, roles, and requests for their specific target application upfront. These tables are structured in a similar format to that of an access control matrix common in various threat modeling methodologies.
- Github Link – https://github.com/SecurityInnovation/AuthMatrix
Burp Suite Professional Download
AuthMatrix requires configuring Burp Suite to use Jython. Be sure to use Jython version 2.7.0 or greater to ensure compatibility.
2. Autorize
Autorize is an automatic authorization enforcement detection extension for Burp Suite. It was written in Python by Barak Tawily, an application security expert, and Federico Dotta, a security expert at Mediaservice.net. Autorize was designed to help security testers by performing automatic authorization tests. With the last release now Autorize also perform automatic authentication tests.
- Github Link –https://github.com/Quitten/Autorize
3. backslash-powered-scanner
This extension complements Burp’s active scanner by using a novel approach capable of finding and confirming both known and unknown classes of server-side injection vulnerabilities. Evolved from classic manual techniques, this approach reaps many of the benefits of manual testing including casual WAF evasion, a tiny network footprint, and flexibility in the face of input filtering.
- Github Link –https://github.com/PortSwigger/backslash-powered-scanner
4. burp-rest-api
A REST/JSON API to the Burp Suite security tool. Upon successfully building the project, an executable JAR file is created with the Burp Suite Professional JAR bundled in it. When the JAR is launched, it provides a REST/JSON endpoint to access the Scanner, Spider, Proxy and other features of the Burp Suite Professional security tool.
- Github Link – https://github.com/vmware/burp-rest-api
5. BurpSmartBuster
A Burp Suite content discovery plugin that add the smart into the Buster through which you can easily find all the hidden resources in a web application! Basically this plugin checks for directories/files, in current URL directories, replace and add extension to current files etc.
- Github Link –https://github.com/pathetiq/BurpSmartBuster
6. BurpKit
BurpKit is a BurpSuite plugin which helps in assessing complex web apps that render the contents of their pages dynamically. It also provides a bi-directional Script bridge API which allows users to create quick one-off BurpSuite plugin prototypes which can interact directly with the DOM and Burp’s extender API.
- Github Link –https://github.com/allfro/BurpKit
7. collaborator-everywhere
A Burp Suite Pro extension which augments your proxy traffic by injecting non-invasive headers designed to reveal backend systems by causing pingbacks to Burp Collaborator.
- Github Link – https://github.com/PortSwigger/collaborator-everywhere
8. C02
Co2 includes several useful enhancements bundled into a single Java-based Burp Extension. The extension has it’s own configuration tab with multiple sub-tabs (for each Co2 module). Modules that interact with other Burp tools can be disabled from within the Co2 configuration tab, so there is no need to disable the entire extension when using just part of the functionality.
- Github Link –https://github.com/JGillam/burp-co2
CO2 is comprised of both a suite of modules as well as standalone versions of some of these modules, either due to popular request or while still in early development prior to being added to the suite. The objectives of all CO2 modules include:
9. distribute-damage
Designed to make Burp evenly distribute load across multiple scanner targets, this extension introduces a per-host throttle, and a context menu to trigger scans from. It may also come in useful for avoiding detection.
- Github Link –https://github.com/PortSwigger/distribute-damage
10. HUNT
HUNT is a Burp Suite extension which identifies common parameters vulnerable to certain vulnerability classes and also organize the testing methodologies inside of Burp Suite.
- Github Link –https://github.com/bugcrowd/HUNT
11. IntruderPayloads
A collection of Burpsuite Intruder payloads and fuzz lists and pentesting methodology. To pull down all 3rd party repos, you need to run install.sh in the same directory of the IntruderPayloads folder.
- Github Link –https://github.com/1N3/IntruderPayloads/blob/master/README.md
Burp Suite Pro
12. Office Open XML Editor
Office Open XML Editor is a burp extension written in Python 2.7 that will allow you to edit Office Open XML(OOXML) file directly in Burp Suite. It will detect request with Office Open XML(docx,xlsx,pptx) and provide you tab to edit XML content which is present inside the document which will futher used to test the XXE attacks.
- Github Link –https://github.com/maxence-schmitt/OfficeOpenXMLEditor
13. PwnBack
Burp Extender plugin that generates a sitemap of a website using Wayback Machine. PwnBack also requires PhantomJS to run. You can download it from here.
- Github Link –https://github.com/P3GLEG/PwnBack
14. SAML Raider
SAML Raider is a Burp Suite extension for testing SAML infrastructures. It contains two core functionalities: Manipulating SAML Messages and manage X.509 certificates.
Burp Suite Tutorial
- Github Link –https://github.com/SAMLRaider/SAMLRaider
15. swurg
Parses Swagger files into the BurpSuite for automating RESTful API testing – approved by Burp for inclusion in their official BApp Store.
- Github Link –https://github.com/AresS31/swurg
16. Burp-molly-pack
Burp-molly-pack is Yandex security checks pack for Burp. The main goal of Burp-molly-pack is to extend Burp checks. Plugins contains Active and Passive security checks.
- Github Link – https://github.com/yandex/burp-molly-pack
Burp Suite Community Download
17. NoPE Proxy
This extension is for those times when Burp just says ‘Nope, i’m not gonna deal with this.’. It’s actually an acronym for Non-HTTP Protocol Extension Proxy for Burp Suite.
- Github Link –https://github.com/summitt/Burp-Non-HTTP-Extension
Nope Proxy also has a port monitor that will only display tcp ports that a remote client is attempting to connect on. This combined with the DNS history can help you find which hosts and ports a mobile app or thin client is attempting to contact so that you can create interceptors for this traffic and proxy it to the real servers.
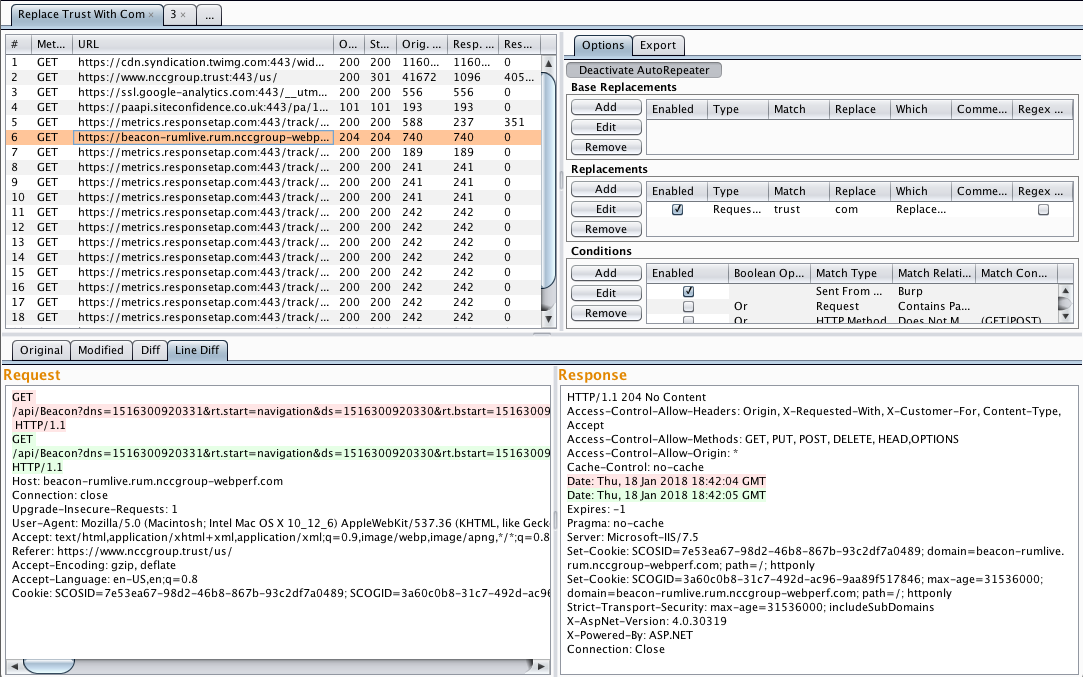
18. AutoRepeater
AutoRepeater, an open source Burp Suite extension that automates and streamlines web application authorization testing, and provides security researchers with an easy-to-use tool for automatically duplicating, modifying, and resending requests within Burp Suite while quickly evaluating the differences in responses.
- Github Link –https://github.com/nccgroup/AutoRepeater
AutoRepeater will only resend requests which are changed by a defined replacement. When AutoRepeater receives a request that matches the conditions set for a given tab, AutoRepeater will first apply every defined base replacement to the request, then will copy the request with the base replacements performed for each defined replacement and apply the given replacement to the request.
19. Uniqueness plugin for Burp Suite
Makes requests unique based on regular expressions. Handy for registration forms and any other endpoint that requires unique values upon every request.
Burp Suite Community Download
- Github Link –https://github.com/silentsignal/burp-uniqueness
